Before going to SQL-INJECTION we should know about SQL and Databases.
Database - Database is nothing but collection of data. In website point of view, database is used for storing user ids,passwords,web page details and more.
For Example -
Oracle
DB servers
MySQL(Open source)
MSSQL
MS-ACCESS
Postgre SQL(open source)
SQLite
SQL:
SQL is nothing but Structured Query Language. In order to communicate with the Database ,we are using SQL query. We are querying the database so it is called as Query language.
What is SQL Injection ?
The goal of SQL injection is to insert arbitrary data, most often a database query, into a string that’s eventually executed by the database. The insidious query may attempt any number of actions, from retrieving alternate data, to modifying or removing information from the database.
This is a hacking method that allows an unauthorized attacker to access a database server. It is facilitated by a common coding blunder. The program accepts data from a client and executes SQL queries without first validating the client’s input. The attacker is then free to extract, modify, add, or delete content from the database. In some circumstances, he may even penetrate past the database server and into the underlying operating system.
Hackers typically test for SQL injection vulnerabilities by sending the application input that would cause the server to generate an invalid SQL query. If the server then returns an error message to the client, the attacker will attempt to reverse-engineer portions of the original SQL query using information gained from these error messages.
What an Hacker can do ?
ByPassing Logins
Accessing secret data
Modifying contents of website
Shutting down the My SQL server
1) Finding Vulnerable Website:
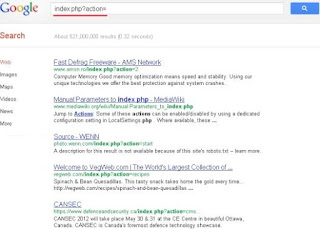
We can find the Vulnerable websites(hackable websites) using Google Dork list. Google dork is searching for vulnerable websites using the google searching tricks. There is lot of tricks to search in Google. But we are going to use "index.php?" command for finding the vulnerable websites.
Some Examples:
index.php?action=
index.php?content=
How to use?
copy one of the above command and paste in the google.com and hit enter.
You can get list of web sites.
We have to visit the websites one by one for checking the vulnerability. Lets start..
Click on first website http://www.amsn.ro/index.php?action=2
2) Check the Vulnerability:
In order to check the vulnerability ,add the single quotes(') at the end of the url and hit enter. There should not space between the number and single quotes.
for ex. http://www.amsn.ro/index.php?action=2'
You get Google Dork List from here
Note : If the page remains in same page or showing that page not found or showing some other webpages. Then it is not vulnerable.
If it showing any errors which is related to sql query,then it is vulnerable.
Lets see more examples,
SELECT * FROM Users WHERE User_Name = ‘” & UserName & “‘ AND Password = ‘” & Password & “’;”
If the tester would enter anup as the strUserName (in the textbox for user name) and amit as strPassword (in the textbox for password), the above SQL statement would become:
SELECT * FROM Users WHERE User_Name = ‘anup’ AND Password = ‘amit’;
If the tester would enter anup’– as UserName and no Password, the SQL statement would become:
SELECT * FROM Users WHERE User_Name = ‘anup’– AND Password = ‘amit’;
If the tester does not know about the user name In such a case, the tester could try common user names like admin or administrator. If none of these users exist in the database, the tester could enter anup’ or ‘x’=’x as strUserName and amit’ or ‘x’=’x as strPassword. This would cause the SQL statement to become like the one below.
SELECT * FROM Users WHERE User_Name = ‘anup’ or ‘x’='x’ AND Password = ‘amit’ or ‘x’=’x’;
Since ‘x’=’x’ condition is always true, the result set would consist of all the rows in the Users table.
If the tester would enter anup’; DROP table users_details;’—as strUserName and anything as strPassword, the SQL statement would become like the one below.
SELECT * FROM Users WHERE User_Name = ‘anup’; DROP table users_details;’ –‘ AND Password = ‘amit’;
This statement could cause the table “users_details” to be permanently deleted from the database.
Though the above examples deal with using the SQL injection technique only the log in page, the tester should test this technique on all the pages of the application that accept user input in textual format e.g. search pages.
SQL injection might be possible in applications that use SSL. Even a firewall might not be able to protect the application against the SQL injection technique.
Read more on Cross Site Scripting
Database - Database is nothing but collection of data. In website point of view, database is used for storing user ids,passwords,web page details and more.
For Example -
Oracle
DB servers
MySQL(Open source)
MSSQL
MS-ACCESS
Postgre SQL(open source)
SQLite
SQL:
SQL is nothing but Structured Query Language. In order to communicate with the Database ,we are using SQL query. We are querying the database so it is called as Query language.
What is SQL Injection ?
The goal of SQL injection is to insert arbitrary data, most often a database query, into a string that’s eventually executed by the database. The insidious query may attempt any number of actions, from retrieving alternate data, to modifying or removing information from the database.
This is a hacking method that allows an unauthorized attacker to access a database server. It is facilitated by a common coding blunder. The program accepts data from a client and executes SQL queries without first validating the client’s input. The attacker is then free to extract, modify, add, or delete content from the database. In some circumstances, he may even penetrate past the database server and into the underlying operating system.
Hackers typically test for SQL injection vulnerabilities by sending the application input that would cause the server to generate an invalid SQL query. If the server then returns an error message to the client, the attacker will attempt to reverse-engineer portions of the original SQL query using information gained from these error messages.
What an Hacker can do ?
ByPassing Logins
Accessing secret data
Modifying contents of website
Shutting down the My SQL server
1) Finding Vulnerable Website:
We can find the Vulnerable websites(hackable websites) using Google Dork list. Google dork is searching for vulnerable websites using the google searching tricks. There is lot of tricks to search in Google. But we are going to use "index.php?" command for finding the vulnerable websites.
Some Examples:
index.php?action=
index.php?content=
How to use?
copy one of the above command and paste in the google.com and hit enter.
You can get list of web sites.
We have to visit the websites one by one for checking the vulnerability. Lets start..
Click on first website http://www.amsn.ro/index.php?action=2
2) Check the Vulnerability:
In order to check the vulnerability ,add the single quotes(') at the end of the url and hit enter. There should not space between the number and single quotes.
for ex. http://www.amsn.ro/index.php?action=2'
You get Google Dork List from here
Note : If the page remains in same page or showing that page not found or showing some other webpages. Then it is not vulnerable.
If it showing any errors which is related to sql query,then it is vulnerable.
Lets see more examples,
SELECT * FROM Users WHERE User_Name = ‘” & UserName & “‘ AND Password = ‘” & Password & “’;”
If the tester would enter anup as the strUserName (in the textbox for user name) and amit as strPassword (in the textbox for password), the above SQL statement would become:
SELECT * FROM Users WHERE User_Name = ‘anup’ AND Password = ‘amit’;
If the tester would enter anup’– as UserName and no Password, the SQL statement would become:
SELECT * FROM Users WHERE User_Name = ‘anup’– AND Password = ‘amit’;
If the tester does not know about the user name In such a case, the tester could try common user names like admin or administrator. If none of these users exist in the database, the tester could enter anup’ or ‘x’=’x as strUserName and amit’ or ‘x’=’x as strPassword. This would cause the SQL statement to become like the one below.
SELECT * FROM Users WHERE User_Name = ‘anup’ or ‘x’='x’ AND Password = ‘amit’ or ‘x’=’x’;
Since ‘x’=’x’ condition is always true, the result set would consist of all the rows in the Users table.
If the tester would enter anup’; DROP table users_details;’—as strUserName and anything as strPassword, the SQL statement would become like the one below.
SELECT * FROM Users WHERE User_Name = ‘anup’; DROP table users_details;’ –‘ AND Password = ‘amit’;
This statement could cause the table “users_details” to be permanently deleted from the database.
Though the above examples deal with using the SQL injection technique only the log in page, the tester should test this technique on all the pages of the application that accept user input in textual format e.g. search pages.
SQL injection might be possible in applications that use SSL. Even a firewall might not be able to protect the application against the SQL injection technique.
Read more on Cross Site Scripting

No comments:
Post a Comment
Thanks for your comment..! Keep commenting for more and more updates. To get post updates subscribe Blog or become a follower of this blog. Thanks Again..!